Configuring Identity Server as IDP for SSO¶
Info
The Single Sign-On with OpenID Connect feature is enabled by default in the ESB.
The Single Sign-On with SAML 2.0 feature in the ESB is implemented according to the SAML 2.0 browser-based SSO support that is facilitated by MWARE IAM (MWARE IAM). This feature is available in any MWARE IAM version from 4.1.0 onwards. Note that MWARE IAM 5.10.0 is used in this guide. MWARE IAM acts as an identity service provider of systems enabled with Single Sign-On, while the Web applications act as SSO service providers. Using this feature, you can configure SSO with SAML 2.0 across the API Publisher and Developer Portal. After configuring, you can access the Developer Portal or API Publisher in a single authentication attempt.
The topics below explain the configurations.
- Configuring Identity Server as IDP for SSO
- Configuring MWARE ESB as Service Provider for Identity Server
- Configuring MWARE IAM as a SAML 2.0 SSO Identity Provider
- Configuring MWARE ESB apps as SAML 2.0 SSO service providers
Tip
In this documentation, MySQL is used as the database to configure MWARE ESB with MWARE IAM. For instructions on replacing the default H2 database with MySQL, see Setting up MySQL.
Configuring MWARE ESB as Service Provider for Identity Server¶
-
Start MWARE IAM.
./wso2server.sh -DportOffset=1Tip
You also can change port offset value in
<IS_HOME>/repository/conf/carbon.xmlfile. Add the following to the<IS_HOME>/repository/conf/deployment.tomlfile.[server] offset = "1"Info
What is port offset?
The port offset feature allows you to run multiple MWARE products, multiple instances of a MWARE product, or multiple MWARE product clusters on the same server or virtual machine (VM). The port offset defines the number by which all ports defined in the runtime, such as the HTTP/S ports, will be offset. For example, if the HTTPS port is defined as 9443 and the port offset is 1, the effective HTTPS port will be 9444.
-
Sign in to the MWARE IAM Management Console UI (e.g.,
https://localhost:9444/carbon).Tip
If you use sign-in pages that are hosted externally to sign in to the Identity Server, give the absolute URLs of those login pages in the
authenticators.xmlandapplication-authenticators.xmlfiles in the<IS_HOME>/repository/conf/identitydirectory. -
Select Add under the Service Providers.
-
Enter a service provider name and click Register.
Tip
In a multi-tenanted environment, for all tenants to be able to sign in to the APIM Web applications, do the following:
-
Click the SaaS Application option that appears after registering the service provider.
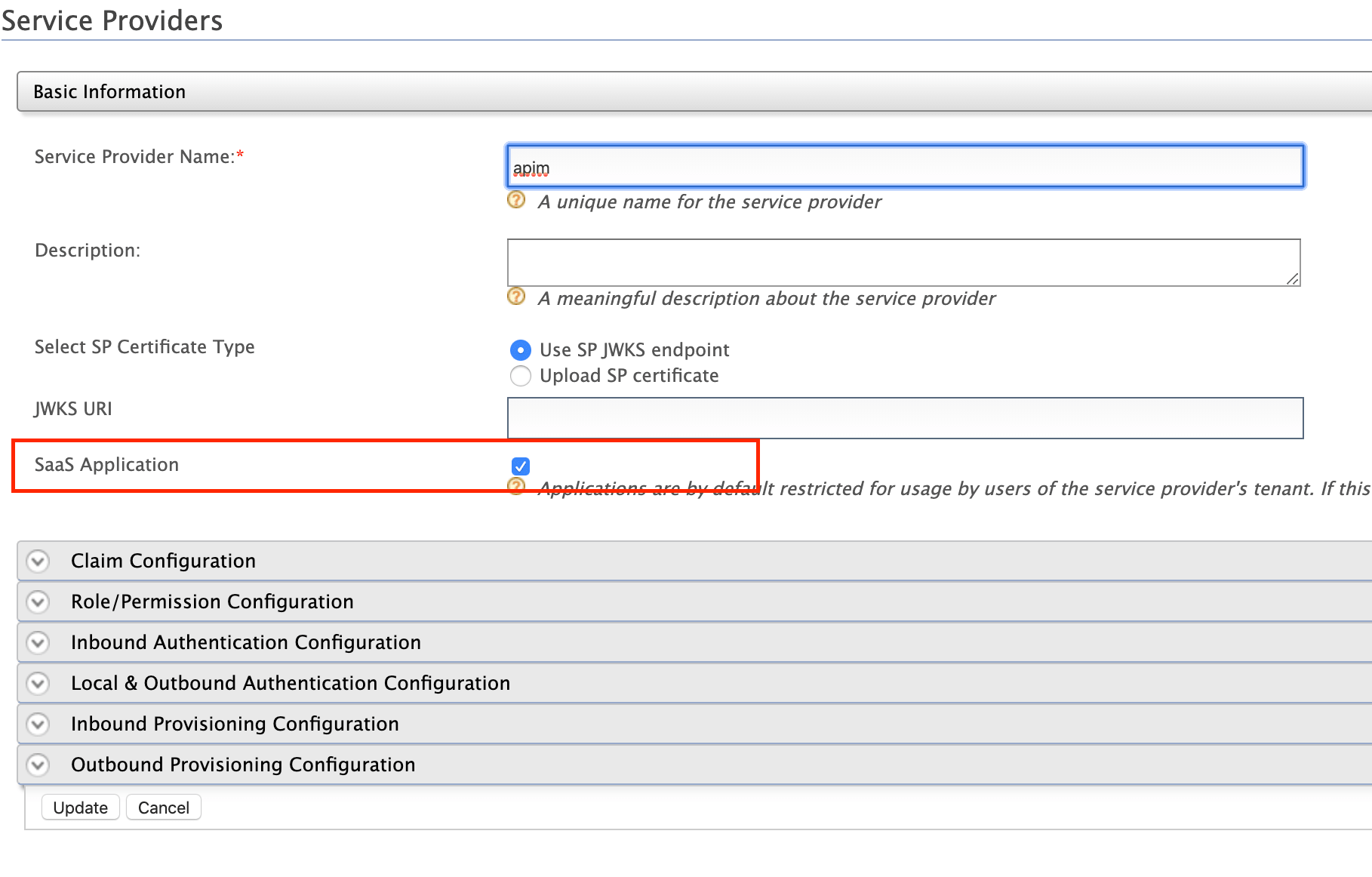 If not, only users in the current tenant domain (the one you are defining the service provider in) will be allowed to sign in to the Web application and you have to register new service providers for all Web applications (Developer Portal and API Publisher in this case) from each tenant space separately.
For example, let's say you have three tenants as TA, TB, and TC and you register the service provider in TA only. If you tick the SaaS Application option, all users in TA, TB, TC tenant domains will be able to sign in. Otherwise, only users in TA will be able to sign in.
If not, only users in the current tenant domain (the one you are defining the service provider in) will be allowed to sign in to the Web application and you have to register new service providers for all Web applications (Developer Portal and API Publisher in this case) from each tenant space separately.
For example, let's say you have three tenants as TA, TB, and TC and you register the service provider in TA only. If you tick the SaaS Application option, all users in TA, TB, TC tenant domains will be able to sign in. Otherwise, only users in TA will be able to sign in. -
Because the servers in a multi-tenanted environment interact with all tenants, all nodes should share the same user store. Therefore, make sure you have a shared registry (JDBC mount, ESB Governance Registry, etc.) instance across all nodes.
You are navigated to the detailed configuration page.
-
-
Click and expand the Claim Configuration section.
- Select
Use Local Claim Dialectcheckbox. - Click on
Add Claim URIbutton next toRequested Claims:lebel and- For Local Claim select
http://wso2.org/claims/groupsfrom the dropdown. - Tick Mandatory Claim checkbox.
- For Local Claim select
- From the dropdown next to
Subject Claim URI:label, selecthttp://wso2.org/claims/username
- Select
-
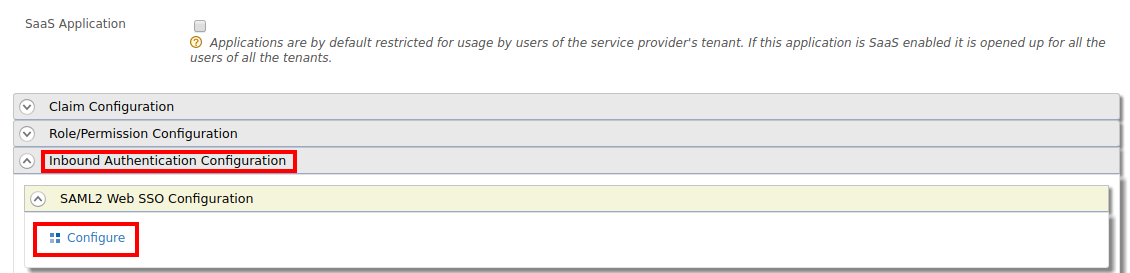
Click and expand the Inbound Authentication Configuration section, click and expand SAML2 Web SSO Configuration, and click Configure.
Note
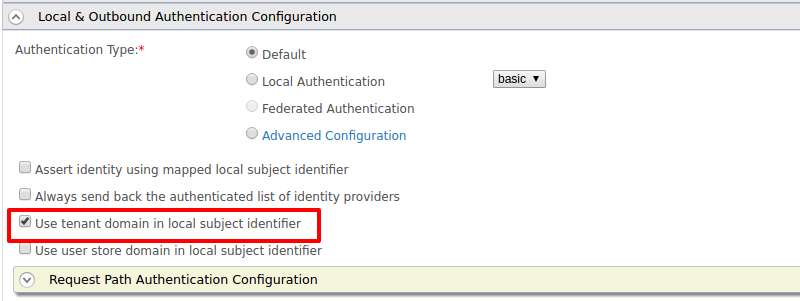
To enable tenant-specific SSO with IS 5.10.0 for the API Publisher and Developer Portal - 1. Click and expand the Local & Outbound Authentication Configuration section. 2. Select Use tenant domain in local subject identifier.
-
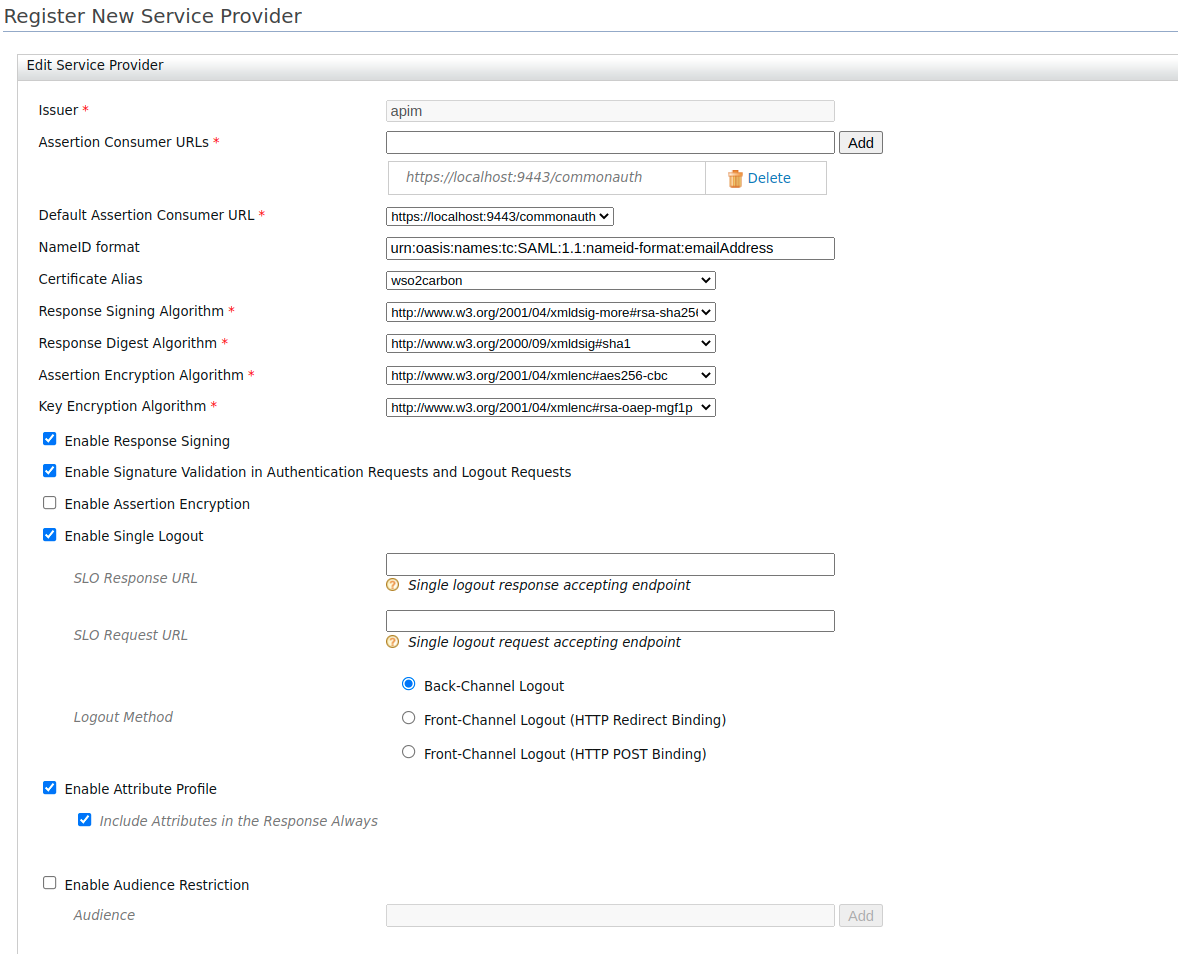
Provide the configurations to register the API Publisher as the SSO service provider.
These sample values may change depending on your configuration.
- Issuer: apim
- Assertion Consumer URL:
https://localhost:9443/commonauth. Change the IP and port accordingly. This is the URL for the Assertion Consumer Services (ACS) page in your running publisher app. - Response Signing Algorithm: rsa-sha256
-
Select the following options:
- Enable Response Signing
- Enable Signature Validation in Authentication Requests and Logout Request
- Enable Single Logout
- Enable Attribute Profile
- Include Attributes in the Response Always
-
Click Register.
Example
-
Upload the public certificate of the ESB by selecting Select SP Certificate Type.
- Create a role:
testRole, create an user with nametestUserand assign the roletestRoleto the created user. This user will be used to sign in to the APIM apps.
Configuring MWARE IAM as a SAML 2.0 SSO Identity Provider¶
Similarly, add the Identity Server as an identity provider configurations in https://localhost:9443/carbon. These sample values may change depending in your configuration.
-
Start ESB
./wso2server.sh -
Sign in to the ESB API Management Console UI (e.g.
https://localhost:9443/carbon). -
Select Add under the Identity Providers menu.

-
Upload the public certificate of Identity Server under Identity Provider Public Certificate.
-
Click and expand the Claim Configuration section, and click and expand Basic Claim Configuration.
- Tick
Define Custom Claim Dialectradio box. - Click
Add Claim Mappingand add the following data.- Identity Provider Claim URI:
http://wso2.org/claims/groups - Local Claim URI:
http://wso2.org/claims/roles
- Identity Provider Claim URI:
- In the dropdown next to the Role Claim URI label, select
http://wso2.org/claims/groups
- Tick
-
Click and expand the Role Configuration section.
- Click Add role Mapping.
- Create a table entry with the following data.
- Identity Provider Role:
testRole - Local Role:
Internal/creator
- Identity Provider Role:
- In the text box next to
Identity Provider OutBound Provisioning Roles:label, type:provision
-
Configure Federated authenticators > SAML2 Web SSO Configurations
- Identity Provider Name: is
-
Service Provider Entity ID: apim
This value can change depending on the Issuer value defined in MWARE IAM SSO configuration above.
-
Identity Provider Entity ID: localhost
- SSO URL:
https://localhost:9444/samlssoChange the IP and port accordingly. This is the redirecting SSO URL in your running MWARE IAM server instance. - Signature Algorithm: RSA with SHA256
- Select the following options:
- Enable SAML2 Web SSO
- Enable Authentication Request Signing
- Enable Authentication Response Signing
- Enable Logout Request Signing
- Single Logout Profile
Example
-
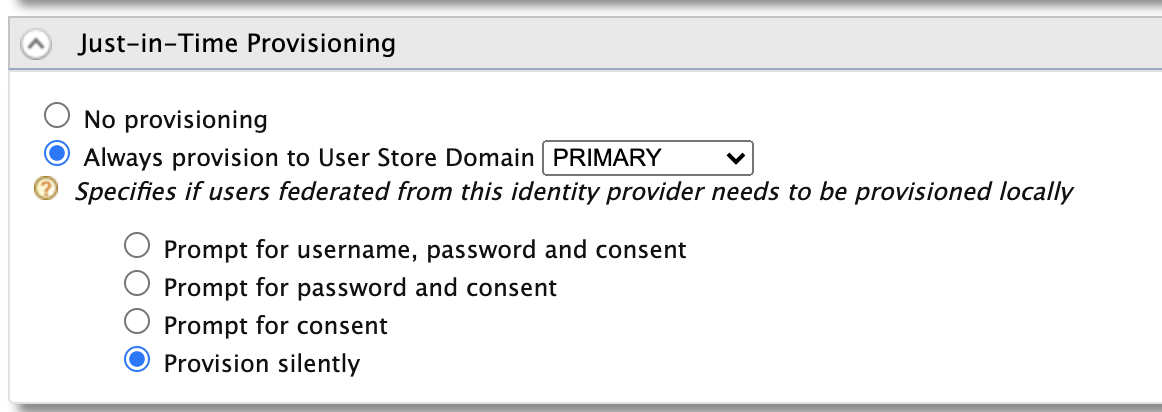
Enable JIT Provisioning users since the userstore is not shared between IS and APIM. The users who will be JIT provisioned should be assigned the relevant role (Internal/creator, Internal/publisher, Internal/subscriber) for them to be able to successfully login to Publisher and Devportal.
-
Click on Register.
Example
Note
Make sure that your service provider configuration in MWARE IAM and the identity provider configuration in MWARE ESB is similarly reflected on each other. Example:
- If the Response Signing Algorithm in MWARE IAM is rsa-sha256, then the Signature Algorithm in MWARE ESB should be RSA with SHA256.
- If you select Enable Single Logout in Identity Server, then select Single Logout Profile in MWARE ESB.
Configuring MWARE ESB apps as SAML 2.0 SSO service providers¶
-
Sign in to the ESB API Management Console UI (
https://localhost:9443/carbon). -
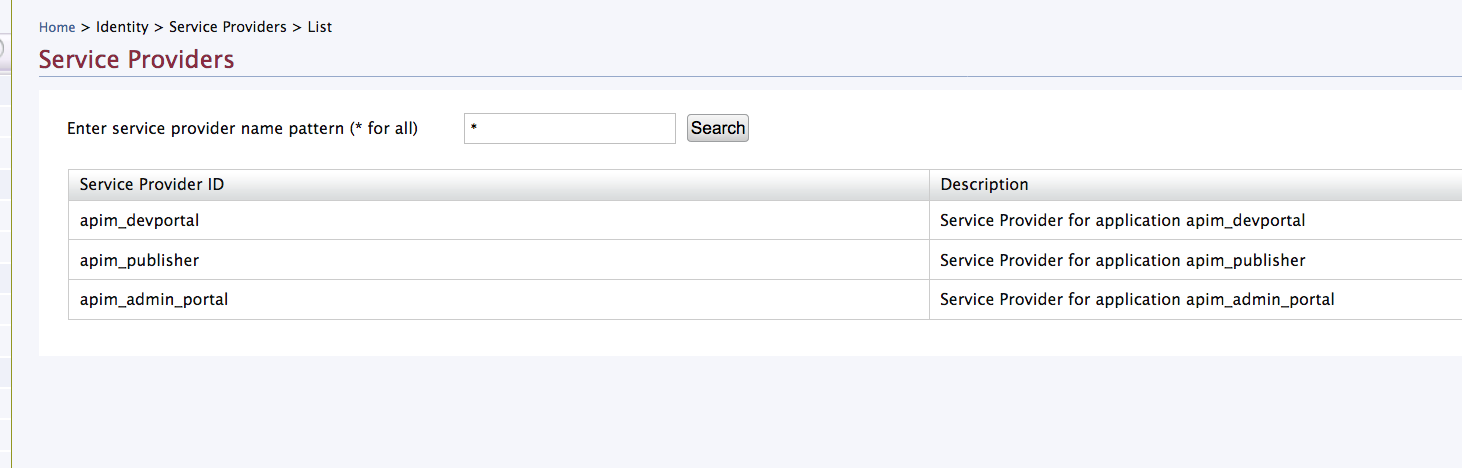
List the service providers, and click Edit on the relevant application for the Publisher, Developer Portal, or Admin Portal.
Note
Note that the Publisher, Developer Portal, and Admin Portal service providers will be listed under Service Providers after you have logged in to each of the portals at least once.
-
Click and expand Local and Outbound Authentication Configuration, select Identity Provider as the Federated Authentication and tick Assert identity using mapped local subject identifier.
-
Click Update.
-
Repeat the above steps (Step 2 to Step 4) to configure SAML2 SSO for any of the Publisher, Developer Portal or Admin Portal applications.
-
Access the API Publisher:
https://localhost:<PORT>/publisher(e.g.,https://localhost:9443/publisher).Observe the request redirect to the MWARE IAM SAML2.0 based SSO login page.
Similarly, access the Developer Portal
https://localhost:<PORT>/devportal(e.g.,https://localhost:9443/devportal) and the Admin Portalhttps://localhost:<PORT>/admin(e.g.,https://localhost:9443/admin) -
Enter user credentials.
If the user authentication is successful against MWARE IAM, it will redirect to the particular Web application with the user already authenticated.
-
If you sign in to the Publisher, then access the Developer Portal application, click Login and verify that the same user is already authenticated in the Developer Portal.
Info
When Just-In-Time Provisioning is enabled, the user details will be saved in the ESB user store. User profile details will be update via federation following each login event. To preserve the system roles (Application/, Workflow/) assigned previously in the user profile without any changes you need to enable the SystemRolesRetainedProvisionHandler.
Add the following to the <API-M_HOME>/repository/conf/deployment.toml file and restart the server.
[authentication.framework.extensions]
provisioning_handler = "org.wso2.carbon.identity.application.authentication.framework.handler.provisioning.impl.SystemRolesRetainedProvisionHandler"Note
Even with SSO enabled, if the users do not have sufficient privileges to access API Publisher/Developer Portal/Admin Portal or any other application, they will not be authorized to access them.
Hence the users who will be JIT provisioned should be assigned the relevant role (Internal/creator, Internal/publisher, Internal/subscriber) for them to be able to successsfully login to API Publisher/Developer Portal/Admin Portal.
Info
For more information on Single Sign-On with MWARE IAM, see SAML 2.0 Web SSO in the MWARE IAM documentation.