Enforce Rate Limiting and Resource Access Policies¶
Rate limiting allows you to limit the number of hits to an API during a given period, typically to protect your APIs from security attacks and your backend services from overuse, regulate traffic according to infrastructure limitations and to regulate usage for monetization. For information on different levels of rate limiting in MWARE ESB, see rate limiting tiers.
Note
This tutorial uses the PizzaShack API, which has GET and POST methods to access it and a rate limiting policy enforced.
Before you begin , follow the Create and Publish an API to create and publish the PizzaShack API and then the Subscribe to an API to subscribe to the API using the Bronze rate limiting tier.
After you created, published, and subscribed to the API, let's see how the API Gateway enforces rate limiting and resource access policies to the API.
-
Sign in to the Developer portal and select the PizzaShack API. Go to the subscriptions tab and make sure we have subscribed to an application or if not subscribe.

-
Go to the Applications tab and go in to the Default Application, click the Production Keys tab and generate an access token. If you already have an access token for the application, you have to regenerate it after 1 hour. Copy the access token after it has been generated.

Let's invoke this API.
-
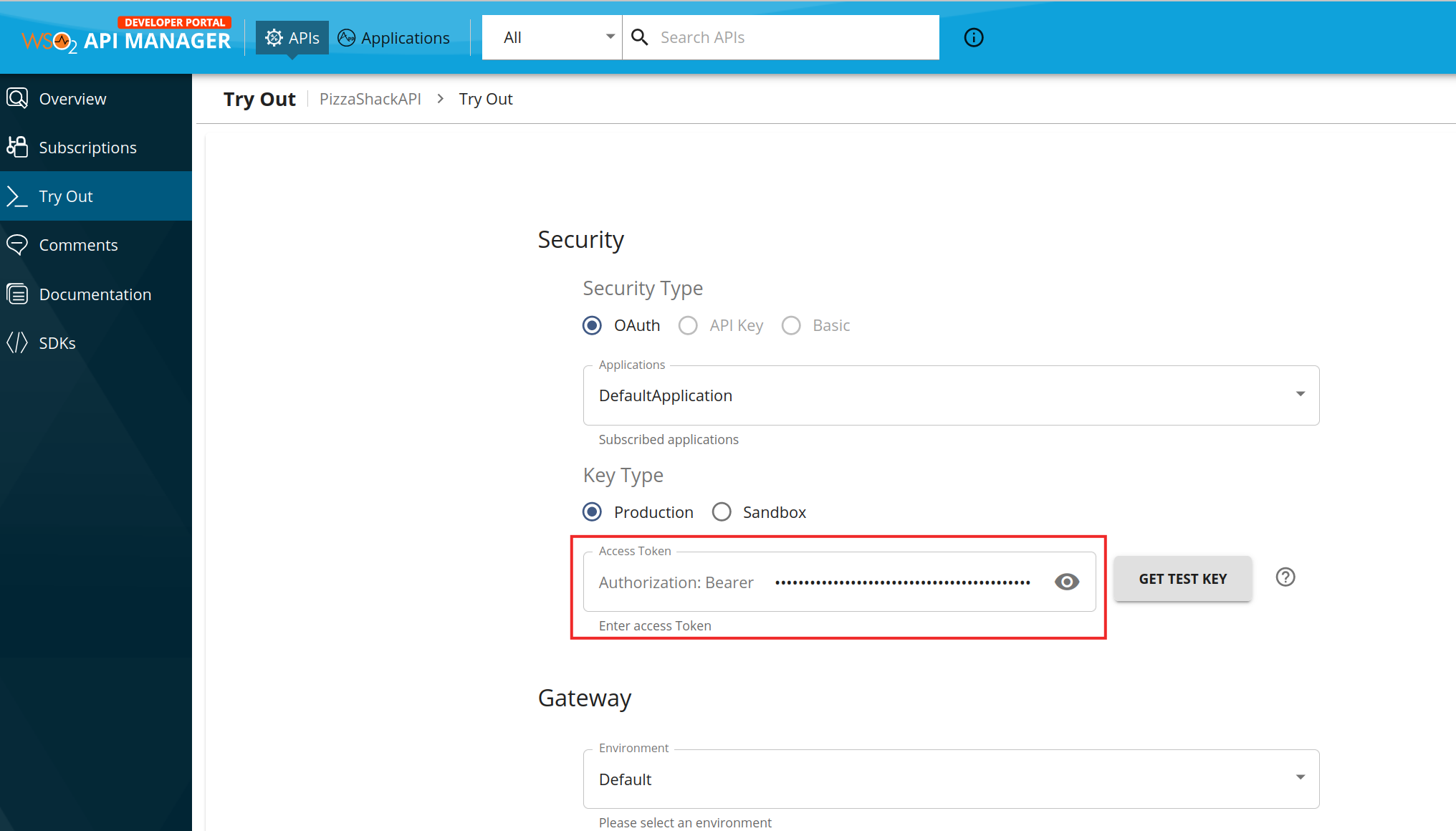
Click on the API, then go to its Try Out tab. Enter the copied access token.
-
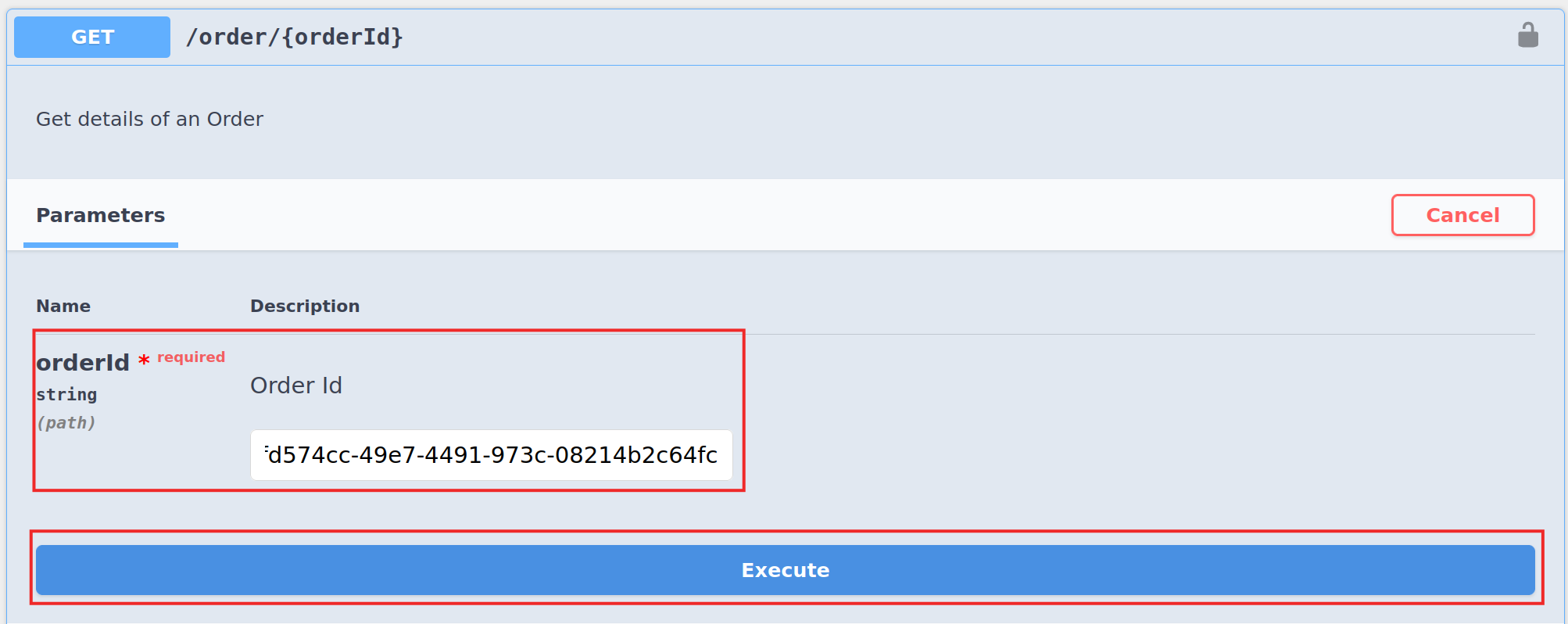
Expand the GET method and click Try it out. Provide the required parameters and click Execute to invoke the API. For example,
OrderID E.g., 7fd574cc-49e7-4491-973c-08214b2c64fc Note the response that appears in the API Console. As we used a valid order id in this example, the response returns a correct order details.

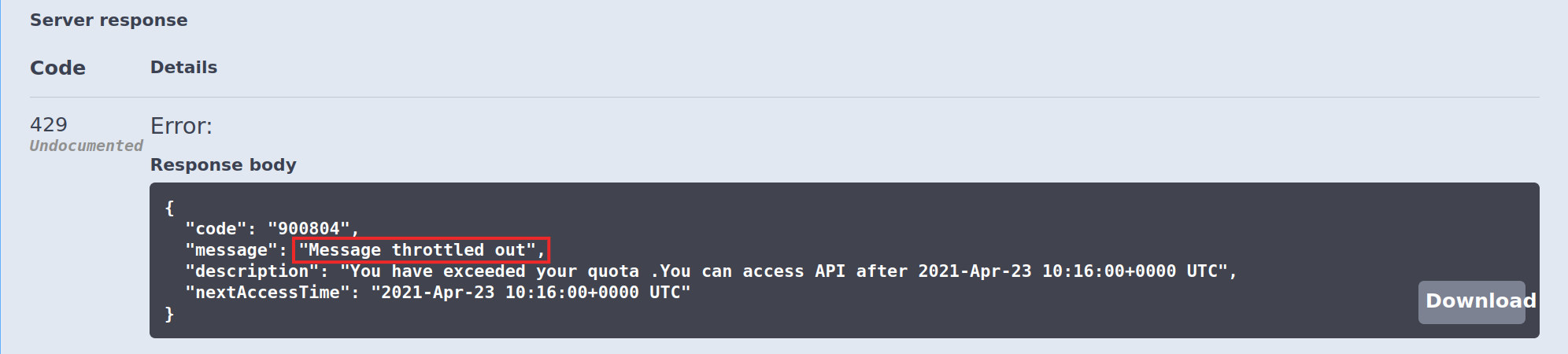
Note that you subscribed to the API on the Bronze rate limiting tier. The Bronze tier allows you to make a 1000 calls to the API per minute. If you exceed your quota, you get a rate limiting error as shown below.